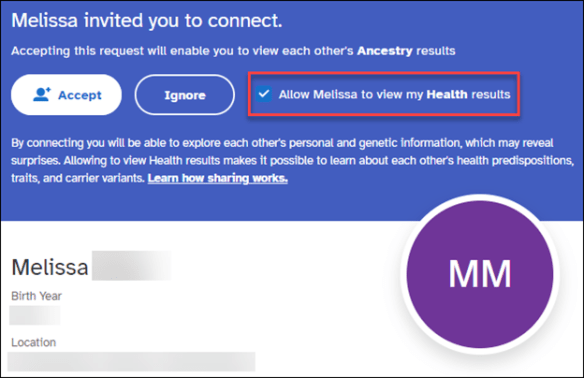
Are you unwittingly exposing yourself and risking your information on Facebook or other social media platforms?
Bad actors are becoming increasingly problematic on social media. There’s been a HUGE UPTICK recently, and we need to keep ourselves safe. Keeping yourself safe also helps keep your friends safe, and vice versa.
Please read this article and follow these steps. Share with your friends and family too.
Please don’t think you’re immune from this. You’re not. Everyone needs to do a checkup periodically.
Sometimes Facebook changes things, and hackers get more wily and cunning all the time. Bad actors are so deceptive now that you may not realize your choices and/or behavior have exposed your information.
Using lots of examples, here’s what this article will do for you:
- Identify and explain new threats and how they work.
- Show you how to modify your privacy settings to prevent unauthorized access.
- Determine if you’ve inadvertently let the bad guys in – and how to shut that door.
- Explain how to stop engaging in risky behavior that you don’t even realize is risky.
Risky behavior on social media is like the flu – people who don’t take proper precautions expose others.
You may think you’re already aware of what’s risky, and what isn’t. Hopefully, that’s true – but when the bad guys change their tactics, we all need to reevaluate accounts, settings, and behaviors.
How Does Exposure Happen
My friends, even friends who should know better, are exposing themselves on Facebook and other social media – and they don’t even realize it.
How?
Lax security settings, Facebook games, innocent-looking questions, and public posts combine to create a toxic slurry of exposure – and you have absolutely no idea that anything is going on beneath the water.
However, it’s absolutely infested with sharks!
Facebook games and questions ARE CRAFTED BY CYBERCRIMINALS.
FULL STOP!!!
You are the target, and your own emotions are the bait.
Yes, I mean you!
I’ve seen almost everyone fall victim to this in one form or another – so you’re not alone. We all learn – hopefully before we have or cause a bad experience.
Did you click on a link you shouldn’t have – before thinking? Have you ever answered any of these seemingly fun questions posted by someone you don’t personally know? Or, someone you DO know whose posting was public? Do you even know if the posting was public?
Here are some examples of bait questions?
- How far away do you live from where you were born?
- Name a song that takes you back to high school?
- Where was your first job?
- Your cowboy (rock star, stripper, animal, you get the idea) name is your middle name. (Then they show you a fun picture.)
- Your first car.
- Thirty random things about me.
If you enter any of that information, you’re doing multiple EXTREMELY RISKY and DANGEROUS THINGS!!!
- Giving potential answers to security questions to cybercriminals who aggregate your data from many seemingly innocent questions.
- Posting the results of those ” fun ” picture games gives cybercriminals access to your personal information, friends, and timeline.
- Giving cybercriminals access to your friend list so they can be targeted too
- Serving as bait for your friends who see your answers because Facebook shows you what your friends and family members answer.
- Serving as bait for your friends who see your AI name or cowboy name or whatever “game” you’ve played. Facebook shows people that you’ve played this game, which serves as an endorsement, especially if people trust you.
Best case, you’re attracting attention to yourself as someone who is naïve and vulnerable. These bad actors are manipulating your emotions, which in turn leads to you oversharing.
You may be hacked, your account cloned, or even lost entirely, AND you’ll be responsible for your friends also engaging in risky behavior.
An even worse case scenario is identity theft.
Here’s the best article I know of that shows several examples. IF YOU DO NOTHING ELSE TODAY, READ THIS ARTICLE, PLEASE!!!
I can hear my mother saying to me, “If everyone else jumped off the bridge, would you too?”
This is the bridge, and I’ll show you why.
That Alluringly Dangerous Bridge
Let’s look at a couple of examples. Different scams work in different ways depending on the goal of the bad actor. We will look at a few so you’re aware.
First, they catch your attention and hope you click before you think.
DO NOT CLICK.
First, lots of professional criminals troll ANY PUBLIC ANSWER.
This post and all replies are public. That little globe means the world can see the post and any comments.
Second, if you click to take this seemingly fun test, you give them lots of information about you, and the results, which are always “wonderful”, post to your feed – which provides “positive feedback” to you and lures your friends. Let’s face it; they will never tell someone they are “below average” because who would play their data-gathering game?
How do they post results to your feed? You give them permission when you click to do the “test,” even though you don’t realize you did that.
Here’s another one.
This has nothing to do with AI. It’s all hooey! Don’t be a willing victim.
NameTests
One of the most popular “games” on Facebook is some derivative of Nametests.
Seriously, do you believe some application can tell you anything useful by selecting three colors? And, ask yourself why anyone would create these “games” and purchase Sponsored Facebook ads to do something “free” for everyone. There is no such thing as a free lunch.
If you’re thinking this is just harmless fun – it’s not.
Do yourself a favor.
Type this into Google: “What is nametests on Facebook?”
Read this article, courtesy of Comparitech, an identity theft prevention company to see what you just gave away. Literally, access to everything in your profile. And you did it willingly. They didn’t have to hack your account. They simply tricked you by luring you with something free that looked like fun.
Ok, now that you’ve done it, Nametests and other similar apps have access to your account, so you need to rescind that permission.
You Just Gave Them Access to Your Friends List
I’ll step you through how to remove anything like this at the end of this article. You’ll also want to change your password and possibly enable two-factor authentication (2FA). You’ve just given some scammer the keys to your kingdom – plus your friends’ too.
That’s not the end, either. In fact, it’s just the beginning.
There’s more.
Questions, Challenges, Feel-Good and Outrage Stories
Emotions are powerful. They cause you to want to comment – or click. You throw caution to the wind. Actually, you simply forget about caution altogether. That’s the goal.
What you need to do is put the brakes on and…
STOP!
Some fishing questions may make you want to reminisce and relive the good old days.
Some look like fun. But ask yourself – why does ANYONE care about that?
Some scare you and trick you into clicking before thinking. They create a sense of either tragedy or urgency.
“Look who died.” “I can’t believe he’s gone.” And before you think, you’ve reacted with “OMG” and clicked and literally given away the farm. Not just your Facebook farm, either. Here’s how this works, with a short video from the Indiana State Attorney General.
What does the Attorney General say? “I don’t click on anything.” Me either! If you see these frightening tagged links from a friend, it means that friend’s account has been hacked or cloned. Contact them but do not message or reply to the account that sent this because you’ll be talking directly to the hacker.
Nostalgic or Emotionally Motivational Postings
Some scams are wonderful stories that make you want to share something affirming.
Some make you nostalgic.
Some make you angry or sad.
Have you seen those found dog scams where the individual claims to have found an injured dog, taken it to the vet, are trying to find the owner and need assistance with the vet bills. There’s an entire Facebook group devoted to identifying fake “found dog” posts, here.
These posts are meant to evoke strong emotions that cause you to forget about safety and just react. It’s called motivation, and these criminals are pros.
Then, because you’re a good person, you share with your friends, or maybe they shared with you so that’s even more encouragement to engage.
Sometimes, the posts don’t even ask you anything directly.
This next post had been up for less than one day, and look how many shares and comments it had.
A couple of weeks later, it had more than 4000 likes, 884 comments, and 559 shares. Just think how many comments it actually has now, scattered around the internet on various people’s pages.
It looks so innocuous and safe, but it isn’t.
You’ve just given these people, whoever they are, an approximate age, and you’ve told them you’re vulnerable to this type of trickery. Hackers gather every tidbit they can about you so that you can be targeted on this and other platforms.
Everything on this account is public, which you can tell by the little globe, meaning everyone anywhere can see what you say and what everyone says.
The recent 23andMe data exposure is a good example of how information can be aggregated and used to breach other accounts. Furthermore, with your age and city location, which may well be available on your Facebook profile page, anyone can use standard internet search tools to find an address, a phone, family members’ names, and more. Much more!
Questions Lists
You may see these question lists posted by your friends and asked to be passed on “for fun.”
Just don’t!!! Remember, your friends and (sometimes) their friends can see responses too. You have NO IDEA who is consuming this information.
Many police organizations have warned against this. Here’s an article.
Anytime you see anything that sounds or smells like these types of posts, OR posts that are public, the first thing that should pop into your mind is STOP – in a bright red neon danger sign.
Yes, I’ve used this exact same image three times now, because you need to remember to STOP. Stop and think before doing anything.
I WANT YOU TO THINK ABOUT THIS IMAGE EVERY SINGLE TIME YOU SEE THINGS LIKE THIS ON FACEBOOK!
How does this toxic material spread like wildfire anyway?
Public Posts Paint a Target on You
The most common danger is fully public posts. Hackers take advantage of public posts when unwary people post or reply publicly.
Public posts, identified by the little globe, open the post up for the entire world to see.
It also opens you up to friend requests and comments from anyone, anyplace.
Scammers troll for anything public and scrape the contents into huge databases organized by name. They know that if you’re naive enough to fall for one scam, you might well be naive enough to fall for another. They’re hoping, anyway.
Not all public posts are scams, but replying to public posts makes you a target.
Here’s an example.
My friend, Sam, reposted this link on his page to be helpful and made it public, meaning everyone can see it from any place. Sam has his security set to “require one friend in common” before you can send them a friend request. Clearly, “Shirley” doesn’t have a friend in common with Sam, so “Shirley” can’t send Sam a friend request. So “Shirley” replied with something “nice,” hoping to entice Sam into sending “Shirley” a friend request so they can gain access to Sam’s account info and friend list.
“Shirley,” who is scantily clad, isn’t “Shirley” at all, but someone trying to gain access to as many people and profiles as possible to scam people.
Comments on Public Posts
I have adopted the policy that I DO NOT, EVER comment on or reply to public posts – even if they’re posted by my friends. Here’s why.
One of my friends has a wonderful history page where he makes several public postings daily. Unfailingly, every single person who replies to his post has one of two things happen:
- If the people who reply or comment (Linda and Douglas here) accept friend requests without a common friend, or if they have a common friend, they get friend requests from scammers (Holman and Amanda here).
If you automatically think you’re safe to accept a friend request if the requester shares a friend with you – think again. Maybe your friend has fallen victim and doesn’t realize it. It can happen to anyone.
- If the commenter does not accept friend requests unless the requester (scammer) and commenter (i.e., the target) have a common friend, then scammers replies to their posting with a compliment and invitation to friend them.
DO NOT REPLY or add them as a friend, and DO BLOCK these people immediately.
Here are some clues to spot fake accounts:
- Extremely attractive or enticing photos
- Single or divorced
- Professional, military or wealthy-looking if male
- Sexualized or seductive if female
- No friends or scads of friends
- Non-substantive public posts
- New account
- Pictures with puppies or animals
- Things to instill confidence – like references to God
Hackers are so “Helpful”
My friend, Pam, had her Instagram Account “hacked” and announced that to the world in a public post on Facebook. She meant to warn her friends, of course.
Truth be told, Pam had not actually been hacked, as her password would (probably) have been changed if she were truly hacked. This recently happened to another friend and he lost his entire Facebook account, including all photos accumulated over more than a dozen years.
Pam’s password was not changed, because she could sign into her account. Her account was actually cloned, meaning a second account was set up using her profile information that looked exactly like her original profile. Then her friends were messaged from the cloned account with links to click that led to malware. Her friends also received friend requests from the cloned “fake Pam” cloned account.
Unfortunately, cloning is very easy to do. Facebook photos are, by default, public. So the bad actor takes your photo, sets up a second account that “looks like you” and then sends your friends friend requests and malicious links. Your friends accept your friend request, not realizing it’s a fraud.
I wonder how a scammer might have obtained access to Pam’s friends’ profile information to determine whom to target.
Any ideas, anyone?
Let’s see:
- Maybe public posts.
- Maybe games
- Maybe answering “questions”
- Maybe Pam’s friend doing one of those things and exposing Pam’s information, too
- Maybe accepting a friend request she shouldn’t have
- Maybe making “too much” public, including her friends list
Let’s see what happened when Pam publicly informed the world that her Instagram account had been hacked! Just in case you think this might be no big deal.
ALL 64 REPLIES WERE FROM HACKERS!
In fact, it’s possible that the original hacker is one of those who responded, offering to “help.”
Here’s the list of all 64 comments, with my commentary in red. Notice that all 64 arrived within two hours. Many of these profiles may, in fact, be the same bad actor.
She went to work and didn’t notice any of this. However, everyone else in the world had the opportunity to reply to one of these hackers, seeking “help,” and her friends might have been lured.
If you comment, you’re at risk too.
Then, someone with a name that includes the word Cyberspy messaged my friend directly.
Oh yeah, this instills confidence, alright.
Unknown people may directly message (DM) you.
Do not reply.
BLOCK THEM ALL!!!
If someone you know messages you with a link, DO NOT CLICK ON IT. Verify another way that they actually sent you something – meaning that their account has not been cloned or hacked. Regardless, I still don’t click on unsolicited links.
Reporting to Facebook
If you know that your friend’s account has been cloned, report to Facebook by clicking on the little three dots on the cloned profile, then “Find support or report.”
Unfortunately, there’s little to be done about the hacker/scammer replies and postings. Reporting any of these fraudulent accounts to Facebook (Meta) is worse than useless – and Facebook is the only one who can take care of it. I have yet to see them take any of these accounts down.
Block all scammers or shady postings or replies.
Your best bet is to NOT fall for any of this.
Bait
This is supposedly a food page, but if you look at the postings, they are all “bait” of one sort or another.
That bait is for you – you’re what they are hoping to snag.
First of all, this post has nothing to do with food. Several posts are of the “who remembers this” type of nostalgia bait, which is particularly attractive to older people who may be less tech-savvy.
Second, they try to make you feel guilty if you’re a grandparent and DON’T “let the world know.”
Third, they are clearly targeting older people, and if you share or post on this, you’ve given them information. Some people actually said how many grandchildren they have and where they live.
Sometimes, older people are more susceptible to scams because they are more trusting.
Stop and Think!
- Why would anyone you don’t know be interested in this information about you?
- Why would you willingly give something this information?
Anyone hear of grandparent call scams? “I’m in trouble. Send money.” Some even go so far as to say they’ve been kidnapped. Here’s what the FCC says about “grandparent scams.”
Scammers who gain access to consumers’ personal information – by mining social media or purchasing data from cyber thieves – can create storylines to prey on the fears of grandparents.
Often the imposter claims to have been in an accident or arrested. The scammer may ask the grandparent “please don’t let mom and dad know,” and may hand the phone over to someone posing as a lawyer seeking immediate payment.
Unfortunately, according to a recent Washington Post article, bad actors can now use artificial intelligence technology “to mimic voices, convincing people, often the elderly, that their loved ones are in distress”.
The article reports that scammers can replicate a voice from just a short audio sample and then use AI tools to hold a conversation in that voice, which “speaks” whatever the imposter types.
I know someone who was targeted this way. They said they could barely understand their granddaughter because she was both crying uncontrollably and hysterical. My friend could make out the word rape. It was terrifying and paralyzing at the same time. Fortunately, her granddaughter happened to walk into the front door as this call was taking place.
What Have You Done?
Are you wondering if you have inadvertently given access to your Facebook page to scammers without realizing it?
You need to check.
Here’s how, step-by-step!
Start by clicking your profile picture, then Settings and Privacy, then Settings, then Apps and Websites – as outlined above and detailed below.
On the left, you’ll see this menu. Scroll towards the bottom.
You’ll see this information at the top, with the following apps that you’ve given access to below.
Click on “remove” to remove unwanted apps. I clicked on “Remove” for Yelp, which displayed additional information. You can remove future access, but you can’t remove any information already shared with the other application.
When you look at an app and see the ability to log in through Facebook, this is actually what you’re doing – sharing a variety of information with that application.
Under “Preferences,” disable the ability to use Facebook to log into third-party apps.
What does signing in through Facebook or Google do? How does it work?
What actually happens when you sign in using Google or Facebook? It’s convenient, but you’re giving away data about yourself that you’re unaware of.
Here’s what LifeLock has to say.
Here’s a list of Facebook privacy settings that you should change now.
Whatever you did in the past can’t be undone, but you can remove the access and prevent anything in the future.
Stop the Thieves – Lock It Down
If you’ve done something risky, you’ll need to take additional precautions.
- Change your password. Don’t reuse passwords.
- If your account has been cloned, change your profile photo so your friends know which account is actually yours.
- Restrict postings to friends only.
- Check for and disable any applications, including games like Nametest.
- Consider implementing 2FA. It’s under “How to keep your account secure” in the Privacy Checkup.
What are your settings?
Let’s check and see.
Privacy Checkup
Facebook makes it easy to do a Privacy Checkup.
Just click on your profile photo, then “Settings and Privacy” and “Privacy Checkup.”
I recommend stepping through every one of these topics and adjusting your permissions.
I recommend locking everything down on your profile.
Begin with “Who can see what you share”.
Scroll to the bottom, where you see “Friends and following.”
CRITICAL
To protect your friends list, and disable anyone else from seeing it, select ONLY ME.
Your next selection under “Who can see what you share” selects the default audience for your Facebook posts, Stories, and limits who can see past posts. This is a critical selection because it determines who can view your posts unless you change this setting on individual posts.
Step through each of the “Privacy Checkup” tabs and do the same for People, Pages and Lists you follow.
Next, check “Profile and Tagging” under the Settings and Privacy Menu on the left-hand side.
Step through each of these sections, especially Posts and Stories, and adjust your privacy.
It’s VERY important to prevent others from viewing your friends list which you’ll find under “Profile and Tagging.”
Some people don’t let anyone post on their profile. I currently do let my friends post, or tag me, but I’m also torn about this setting.
Next, select who can see what others post on your profile?
Make sure to check the rest of the information and if it’s displayed.
I don’t provide any information, such as where I live or went to college – nor do I display my phone number. I get enough spam calls the way it is!
See What They See
Check to be sure your account displays only as much as you want.
On the dropdown menu from your profile picture, go to the Privacy Center and Click on “Manage Your Accounts,” then select “How to clean up your profile.”
Click on “View as” to see your account as someone who is not your friend. Ensure everything is locked down, and you’re not providing information to unknown people.
Best Practices for Safety
Two types of actions are necessary to keep your Facebook account and your friends safe. Both are important – some are account settings, and others are behavioral.
Think of this like driving a car. You need safety equipment like brakes – but you must also know when, where, and how to apply them to keep from crashing.
One alone is insufficient. You need both. You also need to stop and think.
- Lock your account down so that people you don’t know can’t see your information.
- Lock it down so that others can’t see your friend list, so you’re not inadvertently making your friends targets.
- Do not accept friend requests from people you don’t know.
- View everything skeptically.
- STOP every single time you even think about replying to something. Stop, then think. Is the post public? Who wants to know this information, and why would I give it to them?
- If it’s public, DON’T REPLY.
Selecting Privacy for Your Posts
You select a default privacy setting for your own posts. You can also override the default and select a different privacy setting for each post if it differs from your default.
Default settings are found in the “Privacy Checkup,” under “Who can see what you share.”
You can change the privacy selection on each post as you create them. You can also change them later.
Facebook used to retain your selection for the next post, but I don’t think they do that anymore. For example, if I lost my mind for some reason and selected “public,” for this post, the default would have been “public” for subsequent posts too.
I tested this, and it appears that’s no longer the case today. That’s a good thing! You can change any individual post, but your selected default remains in effect.
It’s Time for Spring Cleaning
If your friends have their friend list exposed, they are exposing you to hackers who may want to target you. If your friend’s account is cloned, this is exactly how bad actors know to target you next.
It’s time for spring cleaning on your friend list. Let’s take stock and evaluate.
- Are they your actual friend?
- Why are they on your friend list?
- If you’re undecided, check to see if their friend list is exposed. That’s the tie-breaker. If it is, they are exposing you.
- If someone you know and care about is exposing their friend list, please send them a link to this article.
Let’s Practice
You notice a question on your friend’s feed about the name of your first-grade teacher.
You smile with warm remembrance.
What’s the first thing you’re going to do?
STOP!
THINK!
Public – Look to see if your friend’s posting is public.
If the answer is yes, STOP.
If you answer, you just gave someone information about you that can be combined and aggregated with other information from all of those types of questions you’ve inadvertently answered. Many are security questions and can lead to identity theft.
Games – Next, look to see if it’s one of those games.
If the answer is yes, STOP.
Groups – Next, check to see if the posting is from within a group that you’ve joined. If the the posting is within a restricted group or a non-public Facebook page or group, that may be a more controlled environment, depending on the join criteria and how closely the group is monitored by administrators. I do participate in several closed groups.
Non-public groups are designated by an icon of three people.
Friends Only – If the posting is “friends” only, the two-person icon, the threat is reduced, unless, of course, your friend has inadvertently given access to one of those scam games and, in doing so, has granted access to their entire profile. There’s no way to know. I evaluate the friend and the topic at hand when deciding to reply.
My “go to” response now, on social media, is simply “don’t reply,” unless someone has asked me a direct, non-public, question that makes sense and doesn’t relay any information that even might be useful.
So, if your friend who visited last week asks for a pudding recipe that you made for dessert, and the posting isn’t public, that’s probably just fine.
If your cousin can’t remember your daughter’s middle name and wants it for genealogy, I’m sure that’s fine to answer too, just not in any kind of a public forum. To some degree, Facebook is always public. It’s social media, after all. Message, email or call your cousin with the answer. Don’t post it.
Vigilance as a Way of Life
I know you’re going to hate me for a bit when you see that red STOP as you scroll through your Facebook feed. Right about now, you’re saying, “Roberta, please stop!”
That’s OK. Getting you to see and do that is my entire reason for writing this article. I want it to pop into your mind! I’d rather you be irritated with me than have your account compromised or lost entirely and expose your loved ones in the process. 😊
We must be ever more vigilant as scams and scammers become increasingly sophisticated. Your “scam antennae” should always be up and on high alert.
And yes, I know some of you will tell me that you don’t want to live like that. I understand. Neither do I, but if you want to stay safe – and for your friends and family to remain safe, too – you must be ever-vigilant, alert, and chronically suspicious.
If you see family members acting unsafely on social media, they probably aren’t aware, so please feel free to share this article.
_____________________________________________________________
Follow DNAexplain on Facebook, here.
Share the Love!
You’re always welcome to forward articles or links to friends and share on social media.
If you haven’t already subscribed (it’s free,) you can receive an email whenever I publish by clicking the “follow” button on the main blog page, here.
You Can Help Keep This Blog Free
I receive a small contribution when you click on some of the links to vendors in my articles. This does NOT increase your price but helps me keep the lights on and this informational blog free for everyone. Please click on the links in the articles or to the vendors below if you are purchasing products or DNA testing.
Thank you so much.
DNA Purchases and Free Uploads
- FamilyTreeDNA – Y, mitochondrial and autosomal DNA testing
- MyHeritage DNA – Autosomal DNA test
- MyHeritage FREE DNA file upload – Upload your DNA file from other vendors free
- AncestryDNA – Autosomal DNA test
- AncestryDNA Plus Traits
- 23andMe Ancestry – Autosomal DNA only, no Health
- 23andMe Ancestry Plus Health
Genealogy Products and Services
- MyHeritage FREE Tree Builder – Genealogy software for your computer
- MyHeritage Subscription with Free Trial
- Legacy Family Tree Webinars – Genealogy and DNA classes, subscription-based, some free
- Legacy Family Tree Software – Genealogy software for your computer
- Newspapers.com – Search newspapers for your ancestors
- NewspaperArchive – Search different newspapers for your ancestors
My Book
- DNA for Native American Genealogy – by Roberta Estes, for those ordering the e-book from anyplace, or paperback within the United States
- DNA for Native American Genealogy – for those ordering the paperback outside the US
Genealogy Books
- Genealogical.com – Lots of wonderful genealogy research books
- American Ancestors – Wonderful selection of genealogy books
Genealogy Research
- Legacy Tree Genealogists – Professional genealogy research