Today’s blog is off-topic. It’s not about DNA, but it’s about something every bit as pervasive and something every person who accesses the internet needs to be aware of and understand. Today, we’re going to talk about how e-mail accounts get hacked and hijacked, what the difference is, how those spamy one link e-mails are sent, and both as a person whose e-mail has been compromised and as an e-mail receiver, what you can and should do to protect yourself. If you haven’t already been a victim on one end of this scheme or the other, you likely will be. If you received one of these types of e-mails from me today, you know why I’m writing this article.
So I’m finally taking a few days off. I’m at a retreat. I wake up this morning to a gloriously beautiful spring day and lay there in bed thinking how lucky I am as the sun streams in the window. I reach over to the bedside for my iPhone to see what kind of e-mails have come in overnight, and there is a series of e-mails with the word “Hacked” in their titles, addressed to me. I can tell right there, it’s not going to be a good day.
Yes, the people in one of my address books were receiving those nasty one-line-link e-mails. This one happened to be for Viagra. Worse yet, some of them had clicked on the link, and then when they saw the topic, they realized the e-mail was not really from me, even though the e-mail “from” address was mine, and e-mailed me to tell me so – including my husband who happened to think the Viagra link was hilarious. Good thing he has a sense of humor. Let’s just say I was much less amused.
Hacking vs Hijacking
As it turns out my e-mail address had been hacked. It had not been hijacked. What is the difference you ask? A lot.
A hack job means your password has been compromised and the villain (that’s what we’ll call the hacker) has actually signed on to your account, read any e-mails coming in, looked through your inbox, your saved folders, especially any banking type of folders or one that you’ve named, God forbid, “passwords.” It also generally means that the villain may have also changed your password and then your security questions so now you don’t and can’t get access to your own account.
If you’re lucky, they only send those spamy e-mails. If you’re not lucky, the villain then changes your password and sets about to use you and your account to defraud people. The best example I can think of is the e-mail that almost everyone has received at one time or another that goes something like this:
“Dear Joe, I write you with tears in my eyes. I’m at a hotel in London (or fill in the blank any other city out of the country) and my billfold was stolen. I have no id or any money to pay the bill and I cannot leave the country without paying the hotel bill. Can you please advance me some funds and I will pay you back immediately upon returning home.”
Well, obviously, anyone who replies to “you” is really talking to the villain now, and anyone who DOES advance “you” money is giving it to the villain who lives someplace far from here and is not traceable nor accountable in the US – generally in Russia. Now you would think that this scheme, being as old as mud, would fail miserably, but it doesn’t because there are still naïve people out there who want to help.
If this happens to you and your password has been changed, contact your e-mail provider immediately for assistance as that is the only way you can resolve this situation. Time is of the essence here – so do not delay.
Here’s a link that further discusses this phenomenon and recent Yahoo e-mail compromises.
Ok, that’s hacking.
What Is E-mail Hijacking?
Hijacking is when the villain uses your e-mail address, but not your address book to send spammy or virus filled e-mails to random people who you don’t know and have never communicated with. Basically, they use your e-mail address to “fill in the blank” of the “sending” address. They do not have to gain access to your account to do this. It’s also known as “spoofing” for obvious reasons.
Often, the first symptom you’ll see of this is lots of bounced e-mails that you didn’t send. Many times, these links contain viruses that take over computers, steal the address books from non-cloud-based e-mail systems and worse if the recipient clicks on them. Sometimes, out of curiosity, you’ll click on them in the bounced e-mail too, to see what “you” sent. Don’t do it, no matter how curious you are.
The good news is that with a hijacked e-mail address, the villain has not compromised your actual account. If they have sent the spamy e-mails to your contacts, then your account has been compromised, hacked, but changing your e-mail password (and making sure they have not set up a second or alternate e-mail address under your account) generally takes care of it.
The bad news is that once hijackers have your e-mail address as fodder, there is virtually nothing you can do to stop this type of activity. Frustrating? Indeed. At this point, it’s up to the recipients to be savvy enough to recognize this type of e-mail and to not click on the links, which spread the virus further.
As a recipient of one of these e-mails, one clue that indicates a hacked account versus a highjacked account is to look at the list of recipients. If they are in alphabetical order, meaning that your e-mail address begins with r and you are in the middle of a group of r addresses, and you know the sender, it’s probably a hacked account and the spammer is going through the contact list but only sending to small numbers of recipients at a time so that they will not be caught in the service providers’ spam traps. You need to notify the sender who account has been hacked. If the message looks spammy, but you don’t know the sender and there is no list of recipients, then it’s probably a hijacked e-mail address.
This is much worse with cloud-based e-mail systems.
What Is The Cloud?
A cloud-based system is any system that you sign on to the internet to use and you use online such as Yahoo, Gmail, etc. In other words, not on your own PC. Cloud based systems can be accessed by cell phone or other device that is not a computer.
By contrast, I have a combination of two types of systems. When I’m at home, I use Microsoft Outlook on my desktop system. Outlook downloads all of my e-mails from my internet e-mail provider, Yahoo, in this case, onto my desktop system. This means that all of my customer contacts, thankfully, are only on my desktop system which runs behind a full commercial hardware and software firewall and has the latest and greatest anti-virus/malware software (Norton Internet Security) which is run daily with any updates. Plus my system uploads all of Microsoft’s patches as well, daily, and installs them. Microsoft patches known security holes. Villains exploit these known holes, especially on systems not kept current.
However, when I travel, I can’t get to my home system, of course, so I use Yahoo’s cloud based service where I sign onto their system and read my e-mails online. I can reply and such just like in Outlook. For convenience, I’ve saved the e-mail addresses I use frequently in my online address book. Those are the addresses that were compromised, and only those.
So I know the compromise was not from my system at home, which was turned off in my absence, but from the Yahoo cloud-based e-mail side of things, using my Yahoo address book. If you don’t store any addresses in your address book, there is nothing for the villain to steal. Now, they may still harvest your e-mail address to use in spamming others. Here’s another link about the recent Yahoo attacks along with links from Yahoo about how to protect yourself and steps to take if you have been compromised.
Rich Pasco wrote a great article about both hacking and hijacking, also known as spoofing.
How Did This Happen?
Having spent years in the technology industry, I pretty much stick to the books. I know the rules and abide by them. However, no one is immune, and ultimately, this is like a common cold, it will happen to everyone.
My password was not common, no “real words” but was only 8 letters/numbers. This is, by today’s standards, a mediocre password. There are tools out there called password crackers that can run against your password until it’s cracked, and they are very effective. The only way my password could have been obtained was either utilizing a password cracker, captured using some type of capture software from a public (like hotel) network, or via a Yahoo security breach. It could not have been guessed. Password crackers are free on the internet. More sophisticated ones aren’t free, but for the villain, they are worth every penny. Yahoo’s security issues are discussed in the links above. And yes, I was staying at a hotel.
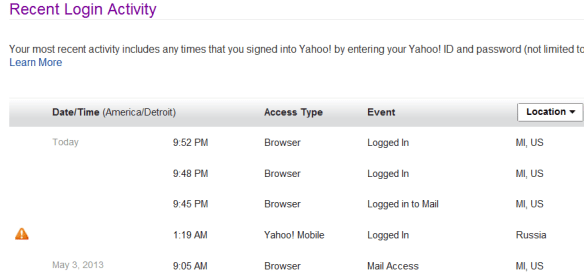
I had a hard time believing my account had been breached, but it had. I signed on to view my recent logins, and sure enough, look at what happened at 1:19 this morning…from Russia. I assure you, that’s not where I was visiting on my retreat. Now since Yahoo knew enough to flag this activity, as you can see below, it would have been very nice if they had notified me.
It’s important to regularly change passwords and to utilize strong passwords. Check this link for further discussion about password strength and vulnerabilities along with how to protect yourself.
10 Ways To Protect Yourself
- Utilize strong passwords – meaning ones that are not your pet, your address, etc. Use nonsense words and numbers combined with capitals and non alpha characters, like sdfg7531+?. Pain in the butt? Yes. More painful than having your account compromised? Nope.
- Never use the same password for multiple accounts. If they can get into one, then you’ve given them a free ticket for all of your accounts. Facebook, Twitter, your bank…what else?
- Don’t keep password or financial information in any e-mail folders. Period. No exceptions. Preferably don’t keep any of that on your computer at all.
- Don’t store e-mail addresses in cloud based e-mail systems. Pain in the butt? Yes. But hackers can only steal what is in your address book or otherwise available to them. By and large, they aren’t going to go through your e-mails individually to obtain addresses. They may, however, delete your entire address book and all of your e-mails, if they are feeling particularly malicious.
- Always keep both anti-virus and mal-ware software up to date on your system. If you clicked on a link that wasn’t what you expected or took you someplace you didn’t plan, run the software immediately.
- Never, NEVER, ever click on a one-line link e-mail no matter who it comes from. It if looks suspicious, reply to the e-mail and ask the person if they really sent it and what it’s about. If you don’t click on it, the worse that will happen is that you’ll miss an e-mail. If you do click on it, you may well infect yourself and others will horrible viruses that can wreak havoc you can only imagine – or maybe can’t even imagine. Conversely, when you send e-mails to people, always put enough verbiage that they know it’s really you. This habit helps people identify messages that might be bogus.
- Don’t use public computers to check e-mail. Be exceedingly careful about using hotel or public wifi sites as well. If you do, change your password afterwards.
- Be extremely vigilant. If something seems wrong or “funny,” it probably is.
- Back your system up regularly. If your system were to be destroyed, you could recover essential items.
- Change your password often. Pain in the patoot? Yep. Better than the alternative? If you’ve ever been on either end of being compromised, you’ll know that it is!
Ok, back to DNA in the next article, I promise!
______________________________________________________________
Disclosure
I receive a small contribution when you click on some of the links to vendors in my articles. This does NOT increase the price you pay but helps me to keep the lights on and this informational blog free for everyone. Please click on the links in the articles or to the vendors below if you are purchasing products or DNA testing.
Thank you so much.
DNA Purchases and Free Transfers
- Family Tree DNA
- MyHeritage DNA only
- MyHeritage DNA plus Health
- MyHeritage FREE DNA file upload
- AncestryDNA
- 23andMe Ancestry
- 23andMe Ancestry Plus Health
- LivingDNA
Genealogy Services
Genealogy Research
- Legacy Tree Genealogists for genealogy research


There’s no such thing as “off topic” in your countless universes, Roberta! I’m so sorry you got hacked & so glad you’ve taken the time to use it to pass along this invaluable information. Beyond identifying the threat, your prevention strategies are right on time. Mil gracias!
Thank you very much for sending this out. It is always refreshing to be reminded of these things. I try to re-run my anti virus and anti malware programs at minimum one time a week just in case.
Ditto many thanks! You explained the process much better than I ever could, and I’ll print your article to save and show to some of my little old lady friends, who don’t know much about hacking/hijacking. 🙂 Brownie
Roberta, Thank you so much. Great article and certainly not off topic and “pervasive as DNA” was a great comparison. I saw that message last night and figured you would get a lot of feedback. They seem to really love Yahoo Groups! Take care and have a restful day.
Roberta, I am most grafeful for this article. As always you have written a terrific piece, one that is very helpful to all. Thank you for taking the time to do that. I for one had no idea of the difference between hacking and hijacking. Thanks for a clear picture!
Pingback: DNAeXplain Archives – General Information Articles | DNAeXplained – Genetic Genealogy